AWS IAM authentication¶
Version added: 6.0.5-4
IAM (Identity Access Management) is the AWS service that allows you to securely control access to AWS resources. Percona Server for MongoDB supports authentication with AWS IAM enabling you to use the same AWS credentials both for it and other components of your infrastructure. This saves your DBAs from managing different sets of secrets and frees their time on other activities.
You can configure AWS IAM for a password-less authentication. Instead of username and password, the user or the application presents the AWS security credentials for authentication, but the secret key is not sent to Percona Server for MongoDB. This significantly increases the security in your infrastructure.
Percona Server for MongoDB supports two authentication types:
User authentication¶
This authentication type is typically used by human operators. Every user account in AWS has the ARN (Amazon Resource Name), which uniquely identifies this account and the user associated with it. During authentication, the ARN is used to verify the user’s identity.
Role authentication¶
This type is typically used for applications / mongo clients. For instance, if your application is running on AWS resources like EC2 instance or ECS (Elastic Container Service) which uses the IAM role assigned to it. Another scenario is to allow users to assume the IAM role and in such a way, grant a user the permissions outlined in the IAM role. The ARN of the IAM role is used to authenticate the application in Percona Server for MongoDB.
For either type of AWS IAM authentication, the flow is the following:
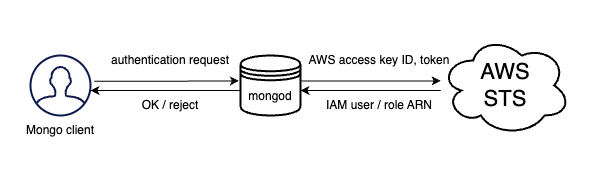
- A
mongoclient (a Mongo shell or an application that talks to Percona Server for MongoDB via a driver) gets AWS credentials from either EC2/ECS instance metadata service, environmental variables or MongoDB URI connection string. -
The
mongoclient constructs the authentication request which includes the AWS access key ID, token and the signature and sends it to Percona Server for MongoDBImportant
The
mongoclient never sends the secret access key to Percona Server for MongoDB. -
Percona Server for MongoDB sends the received credentials to the AWS STS (Security Token Service) for verification
- The AWS STS service validates whether the signature is correct and answers with the user / role ARN that created the signature
- Percona Server for MongoDB looks for the same username as the received ARN in the
$externaldatabase and grants privileges to access Percona Server for MongoDB as defined for the respective user.
Starting with version 6.0.8-6, you can configure the AWS STS endpoint by specifying the setParameter.awsStsHost in the configuration file. This allows you to send requests to the AWS resources of your choice to meet security requirements of your organization and ensure successful authentication.
See also
Configuration¶
For how to configure AWS IAM authentication, see Setting up AWS IAM authentication.